7Feb, 2022
Apache-log4j-Cve-2021-44228 and How It Can Affect Your Sitecore Installation
On December 10th, Apache announced a critical issue with their Log4J library being vulnerable to RCE (Remote Code Execution) attacks, for certain versions of Solr. They listed upgrading Solr as the preferred method for rectifying this issue, but since Sitecore's compatibility is usually closely bound to a limited number of versions, modifying your current installation would be the safest approach.
Who's Affected?
Solr installations versioned 7.4.0 to 7.7.3 and 8.0.0 to 8.11.0 need to be checked and addressed. Versions 5 to 7.3 use log4j 1.2.17 which should be fine, unless you've used non-default logging configurations that include JMS Appender.
Sitecore has also released a security bulletin (SC2021-004-511605) about this, which lists the versions of Sitecore affected, but this is assuming the version of Solr installed is the same as their compatibility table.
What Version of Solr Am I Using?
There's a few ways to make sure of what version you're running. The fastest would be to check the system information, provided you can use the URL: [solr-host]:8983/solr/admin/info/system or [solr-host]/solr/admin/info/system. It really depends on the configuration of your instance.
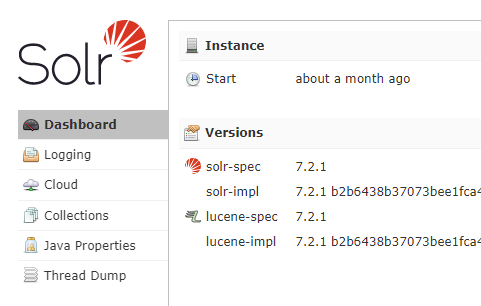
This should give you version information such as:
lucene: {
solr-spec-version: "7.2.1",
solr-impl-version: "7.2.1 b2b6438b37073bee1fca40374e85bf91aa457c0b - ubuntu - 2018-01-10 00:54:21",
lucene-spec-version: "7.2.1",
lucene-impl-version: "7.2.1 b2b6438b37073bee1fca40374e85bf91aa457c0b - ubuntu - 2018-01-10 00:48:43"
},
If you'd prefer an easier approach, you can always use the dashboard at [solr-host]:8983/solr/#/.
What Do I Need to Do?
If your version falls under ones listed above you have some options. The easiest thing to do is ensure your Solr instance is behind a firewall. This should already be the case as Sitecore's Security Guide has this as a step, so most people are safe.
If you want to take the next step, you can edit your solr.in.cmd file to include the following. Don't forget to check your Solr logs after restarting the service once this change is made.
set SOLR_OPTS=%SOLR_OPTS% -Dlog4j2.formatMsgNoLookups=true
That's it! This is a really important issue to check. Articles list vulnerability attempts on monitored endpoints at more than 100 per minute. This is out there, and if your site isn't secure, it's only a matter of time until you're hit.


