13May, 2025
Security Bulletin SC2025-001-7922 Is Needed for Your CM/Standalone Instances
The security bulletin was released on May 12th, 2025 indicating that the issue is related to Telerik UI for ASP.NET AJAX, which is used by Sitecore for UI controls, and impacts XM, XC, XP and Managed Cloud.
The fix is simple, just requiring the following rewrite rules be added to you web.config file.
<rewrite>
<rules>
<rule name="Allow RadAsyncUpload and RadCloudUpload Post Requests" stopProcessing="true">
<match url="Telerik.Web.UI.WebResource.axd" />
<conditions logicalGrouping="MatchAll">
<add input="{UrlDecode:{QUERY_STRING}}" pattern="^type=(rau|rcu)$" ignoreCase="true" />
<add input="{REQUEST_METHOD}" pattern="^POST$" ignoreCase="true" />
</conditions>
<action type="None" />
</rule>
<rule name="Block all GET requests containing Content-Type" stopProcessing="true">
<match url="Telerik.Web.UI.WebResource.axd" ignoreCase="true" />
<conditions logicalGrouping="MatchAll">
<add input="{REQUEST_METHOD}" pattern="^GET$" ignoreCase="true" />
<add input="{HTTP_CONTENT_TYPE}" pattern=".+" ignoreCase="true" />
</conditions>
<action type="CustomResponse" statusCode="403" statusReason="Forbidden" statusDescription="Request blocked" />
</rule>
<rule name="Block PRType and Encoded Attacks" stopProcessing="true">
<match url="Telerik.Web.UI.WebResource.axd" ignoreCase="true" />
<conditions logicalGrouping="MatchAny">
<add input="{UrlDecode:{QUERY_STRING}}" pattern="prtype=" ignoreCase="true" />
<add input="{UrlDecode:{HTTP_COOKIE}}" pattern="prtype=" ignoreCase="true" />
<add input="{REQUEST_METHOD}" pattern="^GET$" negate="true" ignoreCase="true" />
</conditions>
<action type="CustomResponse" statusCode="403" statusReason="Forbidden" statusDescription="Request blocked" />
</rule>
</rules>
</rewrite>
Should This Be a Risk?
Of course, the security patch is going to be applied, but ask yourself, was I at risk? The affected roles are Content Management (CM) and StandAlone.
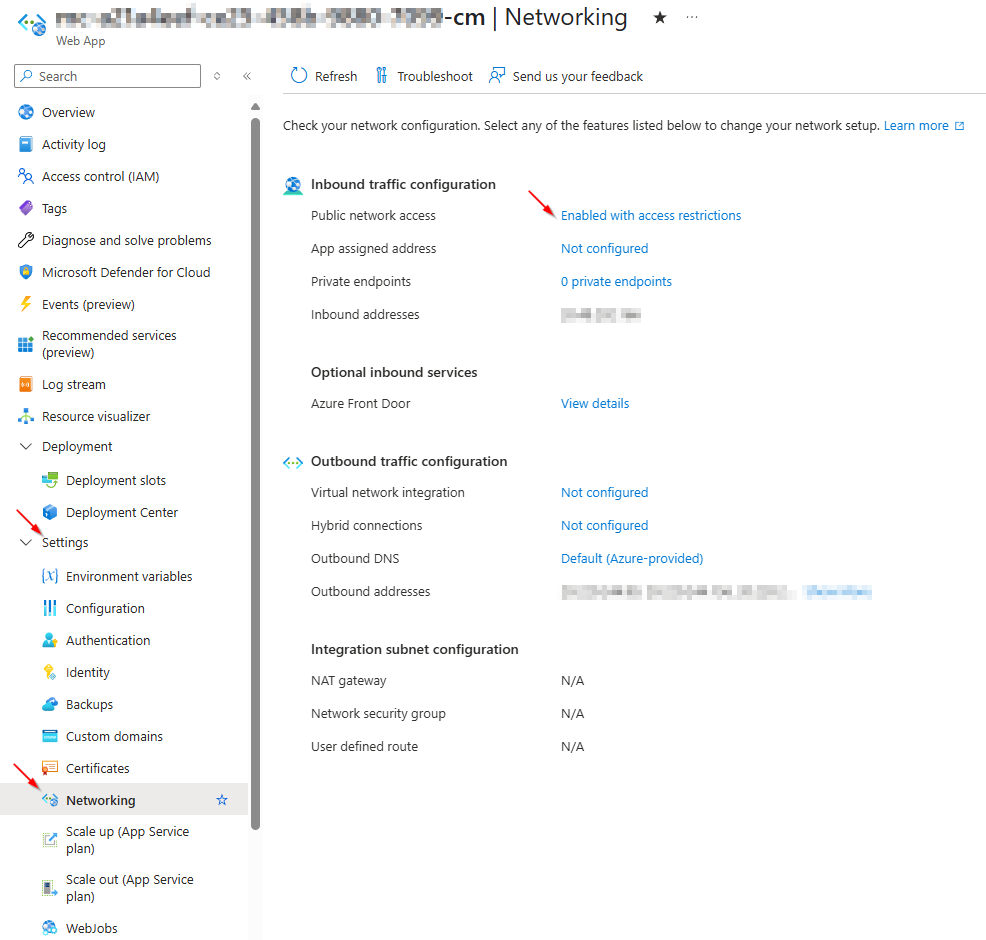
Content Management
This instance should never be publicly accessible. There are difficulties with managed cloud since binding a custom domain with a proxy won't work, so you should set up IP restrictions:
StandAlone
This one goes without saying. This role should never be public for any reason. Even if you are developing using a cloud-based instance, get it private.
Ensure Your Changes Are Applied
Once thing you wan to be careful about is using an external file for redirects like RewriteRules.config since web.config's max size is 250kb. Changes made to these external files are not going to take affect until you recycle the app.
web.config
<system.webServer>
<rewrite>
<rules configSource="RewriteRules.config" />
</rewrite>
</system.webServer>
RewriteRules.config
<rules> <!-- Max file size is 250k --> <rule name="...... </rules>
A quick and dirty way to do this is to just modify your web.config file, which causes the included file's changes to take effect. But if you are using an external file and didn't do this, you're still exposed.
Stay Updated
Be sure to check the security bulletin for updates.


